MG MOTOR SOUTH AFRICA A DIVISION OF SAIC SOUTH AFRICA PROPRIETARY LIMITED
SECURITY COMPROMISE POLICY
Last update: 29 November 2024
- 1.
OVERVIEW
- 1.1
Security Compromises require centralised and swift management and this Policy outlines a framework for responding to such incidents.
- 1.2
It is essential for all Users to comply with this Policy. In the event of a Security Compromise, the incident should be reported to the Information Officer and the Data Privacy Team (see paragraph 6.8 below for the contact details), who will then handle the necessary notifications to the Regulator and affected Data Subjects.
- 1.3
A Security Compromise flowchart is set forth in Annexure A and should assist with contextualising the processes to be followed and implemented in respect of Security Compromises.
- 1.1
- 2.
DEFINITIONS
The following terms bear the meaning given to them here in this Policy and its annexures:
- 2.1
“Data Subject” means any person to whom the specific Personal Information relates, as contemplated in POPIA;
- 2.2
“Information Officer” means the information officer appointed as such by MG Motor in terms of section 56 of POPIA and who will have the ultimate responsibility to ensure that MG Motor complies with the provisions of POPIA. This person is Lex Kriel, who can be contacted at +27 10 976 6666;
- 2.3
“MG Motor” means MG Motor South Africa a Division of SAIC South Africa Proprietary Limited and all its subsidiaries and business areas;
- 2.4
“Personal Information” means information relating to a Data Subject, including the name, race, gender, marital status, address and identifying number of a person, symbol, e-mail address, physical address, telephone number, location information, online identifier or other particular assignment to the Data Subject;
- 2.5
“Policy” means this Security Compromise Policy;
- 2.6
“POPIA” means the Protection of Personal Information Act, 2013, and any regulations or codes of conduct promulgated thereunder;
- 2.7
“Processing” is any activity that involves use of Personal Information. It includes any operation or activity or any set of operations, whether or not by automatic means, concerning Personal Information, including:
- 2.7.1
the collection, receipt, recording, organisation, collation, storage, updating or modification, retrieval, alteration, consultation or use;
- 2.7.2
dissemination by means of transmission, distribution or making available in any other form; or
- 2.7.3
merging, linking, as well as restriction, degradation, erasure or destruction of information,
and “Process” and “Processed” have corresponding meanings;
- 2.7.1
- 2.8
“Regulator” means the Information Regulator established in terms of section 39 of POPIA;
- 2.9
“Security Compromise” means an incident where there has been, or there are reasonable grounds to believe that, Personal Information has been accessed or acquired by an unauthorised person;
- 2.10
“Special Personal Information” includes Personal Information concerning the religious or philosophical beliefs, race or ethnic origin, trade union membership, political persuasion, health or sex life or biometric information of a Data Subject; or the criminal behaviour of a Data Subject to the extent that such information relates to the alleged commission by a Data Subject of any offence; or any proceedings in respect of any offence allegedly committed by a Data Subject or the disposal of such proceedings; and
- 2.11
“Users” include employees, consultants, and service providers who have access to MG Motor's resources, systems, or data as part of their work or services provided to MG Motor and interact with or handle personal information.
- 3.
APPLICATION
This Policy applies to all everyone who uses the MG Motor's resources, systems, or data (in other words Users).
- 4.
KEY CONSIDERATIONS
- 4.1
MG Motor has to comply with POPIA to ensure that measures are taken to keep Personal Information secure, including specific legal obligations around dealing with a Security Compromise. Such legal requirements must be observed in addition to the approach set out in this Policy.
- 4.2
This Policy includes guidelines on how to deal with Security Compromises, including:
- 4.2.1
containment and initial assessment (see paragraph 5);
- 4.2.2
assessing the risks (see paragraph 7)
- 4.2.3
incident classification (see paragraph 8);
- 4.2.4
breach notification (see paragraph 9);
- 4.2.5
remedial action (see paragraph 10); and
- 4.2.6
incident response plan (see paragraph 11).
- 4.2.1
- 4.1
- 5.
WHAT IS A DATA BREACH?
- 5.1
Under POPIA, an incident qualifies as a data breach where there has been, or there are reasonable grounds to believe that, Personal Information has been accessed or acquired by an unauthorised person.
- 5.2
There are three critical elements to extract from this definition:
- 5.2.1
Actual knowledge does not matter: the definition looks at actual or reasonable awareness of an incident. This means that as long as MG Motor is reasonably aware that personal information has been accessed or acquired by an unauthorised person, this will be sufficient to trigger the various notification obligations under POPIA and this policy.
- 5.2.2
The compromise is in the form of access or acquisition of personal information.
- 5.2.3
Unauthorised person: The personal information must have accessed or acquired by someone who was not authorised to process the personal information (whether internal or external to MG Motor).
- 5.2.1
- 5.1
- 6.
CONTAINMENT AND INITIAL ASSESSMENT
- 6.1
An important starting point with any Security Compromise is to consider what steps are required in order to contain it. For example, if the incident involves a form of intrusion (via either internal or external threats) into MG Motor systems then containment action could include:
- 6.1.1
identification of where the intrusion itself is occurring on the systems;
- 6.1.2
closing down such weak points to contain the incident; and
- 6.1.3
prevention of further impact on Personal Information through the compromised systems.
- 6.1.1
- 6.2
Team: Using the risk classification outlined below, where the incident represents a risk that is categorised as a high or medium risk, then a Security Compromise management team should convene to address the incident.
- 6.3
Team authority and scope: The team should have appropriate:
- 6.3.1
internal representation: From the Information Officer and key departments such as, IT, information security, PR/Marketing and legal, and should also have sufficient authority within MG Motor to investigate and address the incident in accordance with this Policy; and
- 6.3.2
external representation: To the extent that MG Motor does not have sufficient capacity internally to address the Security Compromise in accordance with this Policy, MG Motor should appoint necessary external IT/forensic service providers and/or PR (in conjunction with their insurers to the extent that these costs are indemnified under any relevant cyber insurance policy).
- 6.3.1
- 6.4
Insurance notification: The Information Officer and/or the investigation team should immediately, upon becoming aware of a Security Compromise, notify MG Motor’s broker and/or relevant insurer under any applicable cyber insurance policy (or similar policy).
- 6.5
Legal professional privilege: Care should be taken to ensure that the investigation is carried out utilising, to the maximum extent possible, the protection of legal professional privilege. For example, engaging the MG Motor’s legal team and/or appropriate external counsel from the outset may greatly assist in preserving legal professional privilege.
- 6.6
Informing stakeholders: The investigation team should consider which other internal stakeholders should be informed of the incident and at what stage in the investigation process they should be informed.
- 6.7
Confidentiality: The investigation team should also consider keeping the investigation confidential from those (internally or externally) that do not need to be made aware of the investigation (either wholly or in part). This will allow the investigation to continue unhindered, particularly with regard to further scoping of the incident and any activity around it. The extent to which confidentiality should be maintained should also be informed by the requirements of any enforcement authority which has been notified.
- 6.8
Internal incident reporting
- 6.8.1Any individual who suspects that a Security Compromise has occurred, whether via an intentional act or accidental exposure, must immediately report and provide a description of what occurred to the Information Officer.
INFORMATION OFFICER:Information Officer name: Lex Kriel E-mail address: infosupport@mgmotor.co.za Contact number: +27 10 976 6666 - 6.8.2The following non-exhaustive list of possible forms a Security Compromise may take, must be reported immediately, but no later than 24 hours, via e-mail to the above mailbox:
SECURITY EVENT DESCRIPTION OF SECURITY COMPROMISE FOR CLARIFICATION External Breach Defined as a breach where unauthorised individual/s gain access to the internal network of MG Motor, and/or stealing, modifying or deleting Personal Information and/or Special Personal Information, from outside the organisation. This type of breach can be performed by utilising sophisticated cyber-attacks or simple attacks such as a successful phishing email. Internal Breach Defined as a breach where malicious Users or employees of a service provider access the MG Motor network and/or stealing, modifying or deleting Personal Information and/or Special Personal Information, from inside the organisation. This type of breach can be achieved by ill-intentioned or aggrieved Users or service providers’ staff abusing their existing system credentials or installing malicious software onto the MG Motor. Cloud service provider breach Defined as a breach where a cloud service provider or MG Motor cloud-based platform is breached. Examples of such attacks are very similar in nature to an external breach, except that it could also originate at the cloud service provider, directly or indirectly affecting MG Motor. Personally Identifiable Information (PII) breach Defined as a breach achieved by any of the above means as well as procedural failures involving PII-related data. This type of breach must also be considered against the requirements defined in POPIA will require notification to the Regulator. The Information Officer must be consulted in this regard. Ransomware Defined as a breach where a specialised form of malware is installed on the network or a MG Motor-owned device which completely encrypts computer systems into an unusable format. This form of encryption cannot be decrypted without a special key which only the attacker has in their possession and for which a ransom is demanded to decrypt the data. This is usually linked to a defined time period in which to pay the ransom. Device theft / loss Defined as a Security Compromise as a result of the loss or theft of data or equipment on which such data/Personal Information is stored (e.g. loss of laptop, USB stick, iPad / tablet device, or paper record) - 6.8.3
The Security Compromise notification mailbox should be monitored by the Information Officer at all times, to ensure that any Security Compromises that are reported by Users are not missed.
- 6.8.1
- 6.1
- 7.
ASSESSING THE RISKS
- 7.1
The investigation team should assess the risks arising from the Security Compromise. The key driver behind identifying the risk is to assess and consider any potential adverse consequences, for example to:
- 7.1.1
individuals;
- 7.1.2
clients or suppliers; and/or
- 7.1.3
Users.
- 7.1.1
- 7.2
These consequences should consider how serious or substantial the harm might be to anyone within these categories. The risk assessment will inevitably require a classification of the incident (see below) in order to drive the level of response required.
- 7.1
- 8.
INCIDENT CLASSIFICATION
- 8.1
MG Motor treats all the suspected Security Compromises or actual Security Compromises very seriously.
- 8.2
Any Security Compromise may be classified according to the severity of risk as high, medium or low basis harm to individuals whose confidentiality or Personal Information has been breached, reputational damage to MG Motor, legal action from Data Subjects or regulators. This can vary from case to case according to the situation.
- 8.3
Incidents should be classified according to severity of risk, considering the following:
- 8.3.1
Level 1: High risk of:
- 8.3.1.1
harm to individuals whose confidentiality or Personal information has been breached;
- 8.3.1.2
reputational damage to MG Motor; and
- 8.3.1.3
legal action from Data Subjects or regulators.
- 8.3.1.1
- 8.3.2
Level 2: Medium risk of:
- 8.3.2.1
harm to individuals whose confidentiality or Personal information has been breached;
- 8.3.2.2
reputational damage to MG Motor; and
- 8.3.2.3
legal action from Data Subjects or regulators.
- 8.3.2.1
- 8.3.4
Level 3: Low risk of:
- 8.3.3.1
harm to individuals whose confidentiality or Personal information has been breached;
- 8.3.3.2
reputational damage to MG Motor; and
- 8.3.3.3
legal action from Data Subjects or regulators.
- 8.3.3.1
- 8.3.1
- 8.4Classification of Risks
Likelihood of
occurrence of
the data breachSeverity Low Medium High Very unlikely Level 3 risk Level 3 to level 2 risk Level 2 to level 1 risk Unlikely Level 3 risk Level 2 risk Level 1risk Likely Level 2 risk Level 1 risk Level 1risk Very likely Level 1 risk Level 1risk Level 1risk - 8.5Information Sensitivity Classification
CATEGORY OF INFORMATION SENSITIVITY RISK LEVEL Special Personal Information High Level 1 Financial information (e.g. payment card details, billing information, banking information) High Level 1 Children's Personal Information Medium to high Level 1 Personal identifiable information (e.g. names, addresses, identity numbers) Medium to high Level 2 Login credentials (e.g. usernames, passwords) Medium Level 2 Information that is in the public domain Low Level 3 - 8.6
In practice the investigation may provide insight into the level of risk as a result of having contained the Security Compromise and after the initial stages of the assessment. However, during this particular stage and in order to evaluate the risk, the investigation team should consider the following non-exhaustive list of factors:
- 8.6.1
what information has been confirmed to have been impacted by the Security Compromise or is suspected to have been impacted as a result of the Security Compromise?
- 8.6.2
who is affected and what is the likelihood of any harm as a result of the incident?
- 8.6.3
where was the information being Processed and handled?
- 8.6.4
which MG Motor department/ area/ business /subsidiary /office/ or other entity within the group is responsible for such Processing and handling?
- 8.6.5
what was determined to be the cause of the Security Compromise?
- 8.6.6
what was determined to be the extent or reach of the Security Compromise?
- 8.6.1
- 8.7
Regulatory reporting: The investigation will require consideration of the reporting requirements under POPIA and other ancillary South African rules. For that, the Information Officer should be involved from the outset.
- 8.8
Protective measures: Other factors of the investigation will focus around whether or not the Personal Information involved in the incident was subject to specific protective measures. For example:
- 8.8.1
was encryption used?
- 8.8.2
what levels of encryption were used?
- 8.8.3
was the encryption technology and the standard used sufficient to safeguard the Personal Information against any risks as a result of the Security Compromise?
- 8.8.1
- 8.9
As part of the investigation team’s role they will need to establish exactly what information has been compromised and whether or not the incident took place within the control of MG Motor or whether the risk materialised within the control of its third parties.
- 8.10
In the case where the risk materialised within the control of a third party, the team will need to assess what obligations and responsibilities (i) may flow under POPIA; and (ii) are set out in the contract (for example, the operator agreement) between MG Motor and the third party.
- 8.1
- 9.
LEGAL NOTIFICATION
- 9.1
As a result of the investigations carried out by MG Motor and in the event that it is reasonably established that there has been unauthorised access or acquisition of Personal Information of any Data Subject (i.e. a Security Compromise), MG Motor:
- 9.1.1
is obligated in terms of POPIA to report the Security Compromise to the Regulator and the affected Data Subjects as soon as reasonably possible after the discovery of the Security Compromise, taking into account the time it takes to spend on the initial containment, and the legitimate needs of law enforcement;
- 9.1.2
should report to its insurers, in terms of any applicable insurance policy as soon as reasonably possible;
- 9.1.3
must take into account any reporting obligations to other entities or organisations if required by specific legislation - for example, the South African Police Service, the National Intelligence Agency; and
- 9.1.4
must consider its reporting obligations to other entities or organisations, on an optional basis or if required by any contractual obligation - for example customers or clients, if deemed appropriate by the public relations department, senior management and the Information Officer.
- 9.1.1
- 9.2
The team should consider seeking appropriate expert advice on the notification requirements.
- 9.3
Notification to the Regulator in terms of POPIA
- 9.3.1
The Regulator must be notified of all unauthorised access or acquisition of Personal Information of any Data Subject, as soon as reasonably possible, which notification must include:
- 9.3.1.1
a description of the possible consequences of the Security Compromise;
- 9.3.1.2
a description of the measures that MG Motor has taken, and intends on taking, to address the Security Compromise;
- 9.3.1.3
the identity of the unauthorised person/s (if known); and
- 9.3.1.4
a recommendation with regard to possible measures that should be taken by affected Data Subjects to mitigate any possible adverse effects of the Security Compromise.
- 9.3.1.1
- 9.3.2
The notification to the Regulator must be made on Annexure A of Form SCN1, which is available on the Regulator’s website: https://inforegulator.org.za.
- 9.3.3
The Information Officer will be required to use the prescribed form. Failing to use the prescribed form to notify the Regulator may result in the notification being regarded as non-compliant.
- 9.3.4
The notification must be comprehensive and the Information Officer must attach the relevant documents in support of the notification and include further information if there is not enough space on the form as an Annexure to the form and sign each page.
- 9.3.1
- 9.4
Notification to Data Subjects in terms of POPIA
- 9.4.1
In certain instances the notifications to the affected Data Subjects may have to be delayed if the South African Police Service, the National Intelligence Agency and/or the Regulator determines that notification will impede a criminal investigation related to the Security Compromise.
- 9.4.2
The notification to the affected Data Subjects must be in writing and communicated to the Data Subject in at least one of the following ways:
- 9.4.2.1
mail;
- 9.4.2.2
e-mail;
- 9.4.2.3
placement on the website of MG Motor;
- 9.4.2.4
publication in the news media; or
- 9.4.2.5
as may be directed by the Regulator.
- 9.4.2.1
- 9.4.3
The notification must provide enough details to enable the impacted Data Subjects to take precautions against any negative effects of the Security Compromise. This may include, if known, the identity of the unauthorised person who may have accessed or acquired their Personal Information.
- 9.4.1
- 9.1
- 10.
EVALUATION AND RESPONSE
- 10.1
Evaluation: It is essential for MG Motor to conduct an appropriate and thorough investigation. MG Motor must then analyse the risks arising from a Security Compromise and the effectiveness of the systems and controls within MG Motor. Throughout the process, MG Motor should question why the particular weaknesses or failure points led to the Security Compromise arising. For example, if the Security Compromise was caused entirely by or even in part attributed to a systemic organisational or technical problem within MG Motor then merely containing the Security Compromise and otherwise continuing with “business as usual” would not be acceptable in the eyes of the Regulator.
- 10.2
Response and implementation: The investigating team should ensure that the lessons learnt from the incident should be incorporated into strengthening the existing technical and/or organisational security measures.
- 10.3
Security Compromise closure and record: Documentation and records of Security Compromises must be compiled by the Information Officer and retained centrally for historical, trend, and legal purposes. Documentation must detail the Security Compromise’s impact, root cause (if known) and any implemented or future activities to be performed which aim to prevent future occurrences of similar incidents.
- 10.1
- 11.
INCIDENT RESPONSE PLAN – CHECKLIST
- 11.1
All Security Compromises must be treated as strictly confidential, and not communicated to any Users or external parties without authorisation.
- 11.2
All evidence must be preserved, handled carefully and not compromised.
- 11.3
All Security Compromises must be evaluated and classified (see paragraph 7). The Security Compromise event/incident level can be reviewed and adjusted appropriately in accordance with any developments regarding the investigation of the Security Compromise.
- 11.4
If the Security Compromise needs to be reported to the Regulator or Data Subjects, refer to the process set forth in paragraph 9.
- 11.5
The incident response plan must comprise of a documented, methodical approach towards addressing a Security Compromise which should include factors such as the following:
- 11.5.1
Evaluation of risk: This factor should address assessing what actually happened, which includes:
- 11.5.1.1
a determination of what Personal Information was involved;
- 11.5.1.2
establishing the cause and the extent of the Security Compromise;
- 11.5.1.3
determining who is actually affected by the Security Compromise; and
- 11.5.1.4
consider the extent to which those affected by the Security Compromise will suffer any harm or otherwise assess the consequences of the Security Compromise.
- 11.5.1.1
- 11.5.2
Containment and initial assessment: The focus in respect of this factor should include:
- 11.5.2.1
containing the Security Compromise;
- 11.5.2.2
assigning responsibilities to investigate the incident;
- 11.5.2.3
assembling and authorising the investigation team to act;
- 11.5.2.4
notifying defined internal stakeholders; and
- 11.5.2.5
considering notification to any other third parties as may be required.
- 11.5.2.1
- 11.5.3
Notification: This factor should address:
- 11.5.3.1
allocating responsibilities;
- 11.5.3.2
seeking expert assistance and advice;
- 11.5.3.3
notifying the Regulator as soon as reasonably possible after discovering the Security Compromise;
- 11.5.3.4
notifying all affected Data Subjects, if identifiable, unless told not to by the Regulator and/or law enforcement;
- 11.5.3.5
choosing the methods of notification such as mail, email, press release or website publication; and
- 11.5.3.6
including sufficient information in the notification to allow the affected Data Subjects to take protective action against the potential consequences of the Security Compromise.
- 11.5.3.1
- 11.5.4
Remedial Action: This factor should address:
- 11.5.4.1
ensuring that the risk register for MG Motor is updated with all Security Compromises and suspected Security Compromises (near-misses);
- 11.5.4.2
updating policies and procedures to ensure there will be measures to prevent the recurrence of the same or similar Security Compromise;
- 11.5.4.3
reviewing any issues raised around service delivery/third party partners;
- 11.5.4.4
testing the revised incident response plan; and
- 11.5.4.5
finalising and implementing the incident response revised plan and conducting appropriate training and/or mock tests.
- 11.5.4.1
- 11.5.1
- 11.1
- 12.
CONSEQUENCES OF NON-COMPLIANCE
- 12.1
It is essential that all Users comply with all relevant parts of this Policy. Any failure to comply with this Policy could have serious consequences for MG Motor and Users. Failure to comply may lead to: (i) disciplinary action, including summary dismissal (without notice or a payment in lieu of notice) for serious or repeated breaches; (ii) civil or criminal proceedings; and/or (iii) personal liability for those responsible.
- 12.2
It may also be the case that a User’s conduct and or actions may be unlawful and MG Motor reserves the right to inform the appropriate authorities. Actions may result in civil or criminal proceedings. Users should note that in some cases they may be personally liable for their actions and or conduct.
- 12.1
- 13.
POLICY REVISION
This Policy has been reviewed and approved by the Information Officer, and is subject to change without prior notice.
Annexure A DATA BREACH FLOWCHART
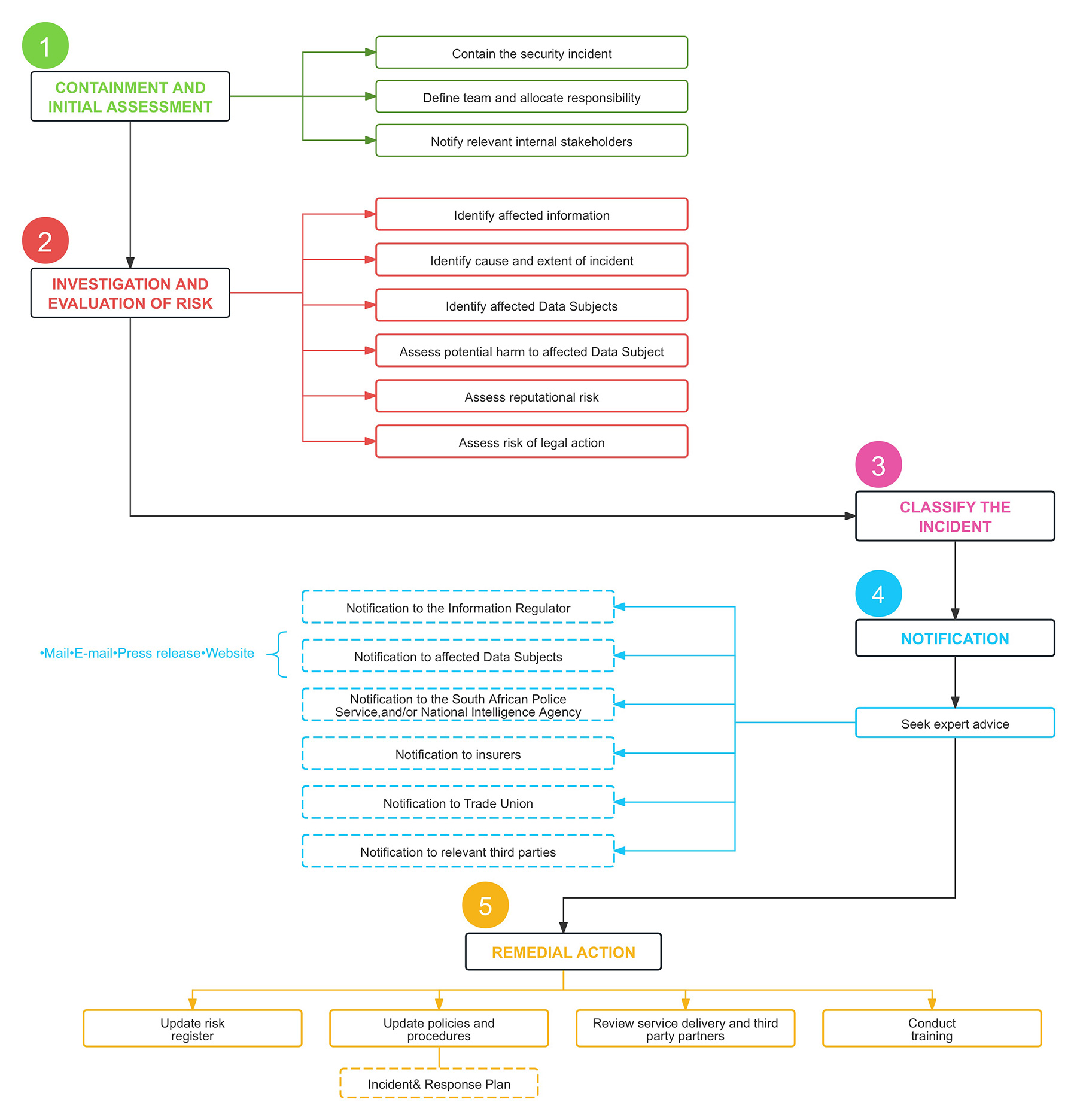
Refer to the Security Compromise Policy for detailed guidelines
Some steps may be taken at the same time as others
